A Quick Overview of Traefik Hub
I learned about Traefik Hub a few months back when I was checking their change log of 2.7 version. Their doc did not tell me what Hub Agent was and how to run it. I thought Traefik team might reserve this information on purpose so I did not dig further at the time.
One of my colleagues shared Traefik’s latest blog Announcing Traefik Hub with me a few days ago and it reminds me of this new product. So I registered an account and tested it out. I would like to share my experience and initial thoughts with you.
TL;DR: Traefik Hub can be used to expose your local services to the internet via their edge network. Their edge network can then apply authentication to the requests coming to your applications.
Sounds familiar? Yep, it does the same thing as Ngrok and Cloudflare tunnel.
Let’s start our test. First of all , we need to register our account at https://hub.traefik.io/.
Once you log in, you would see this welcome page. I quite like this interface, very clean and the color theme is very pleasing to my eyes.
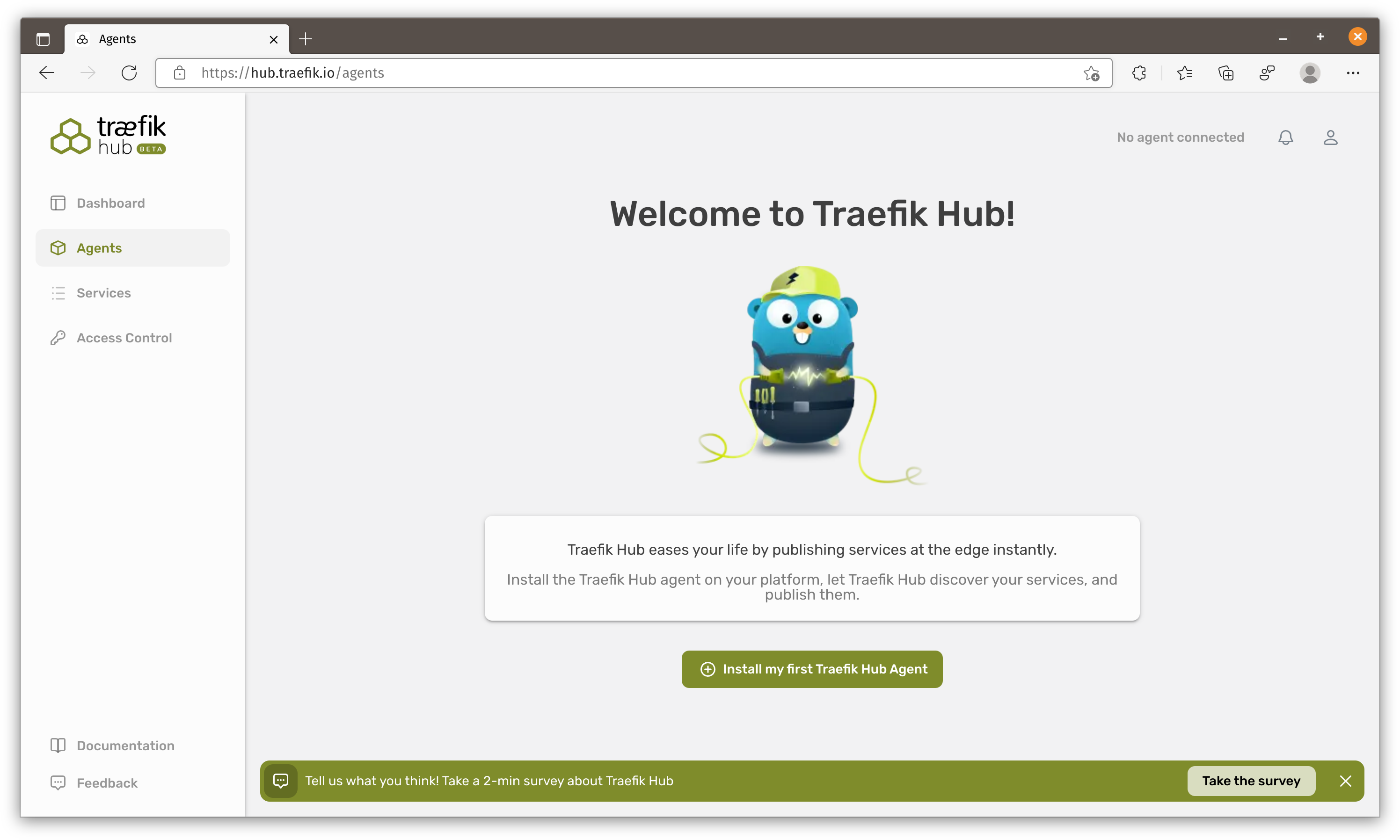
Create Hub Agent
Let’s create our first Traefik Hub Agent.
They provide commands to install Traefik hub on kubernetes, docker, docker-compose and docker-swarm. Unlike Ngrok or Cloudflare, you would need to install two containers (Traefik and Traefik hub) to make this work.
When a service requires more than 1 container, I normally use docker-compose to mange all of them.
You should notice the docker instruction creates a
traefik_hubnetwork and docker-compose instruction does not.
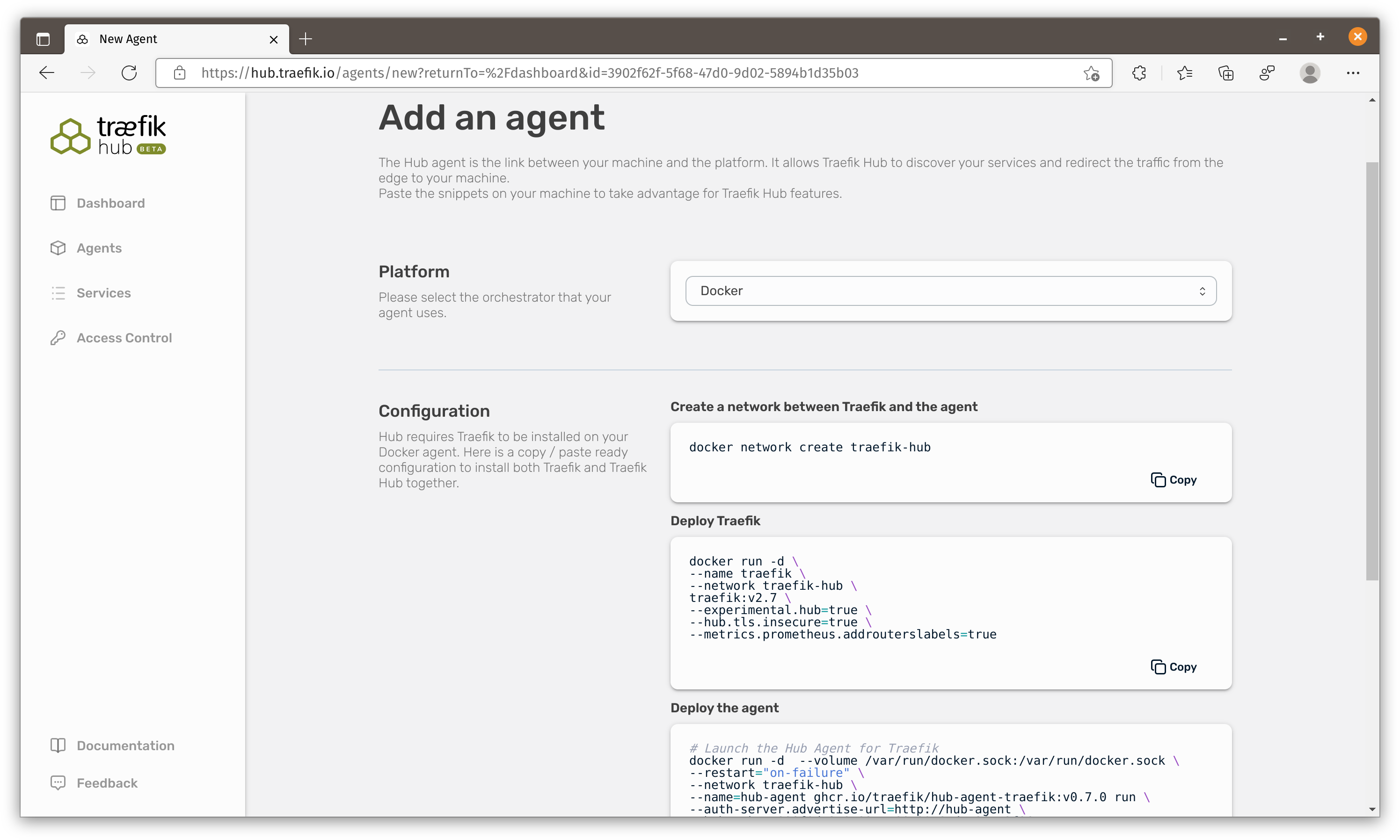
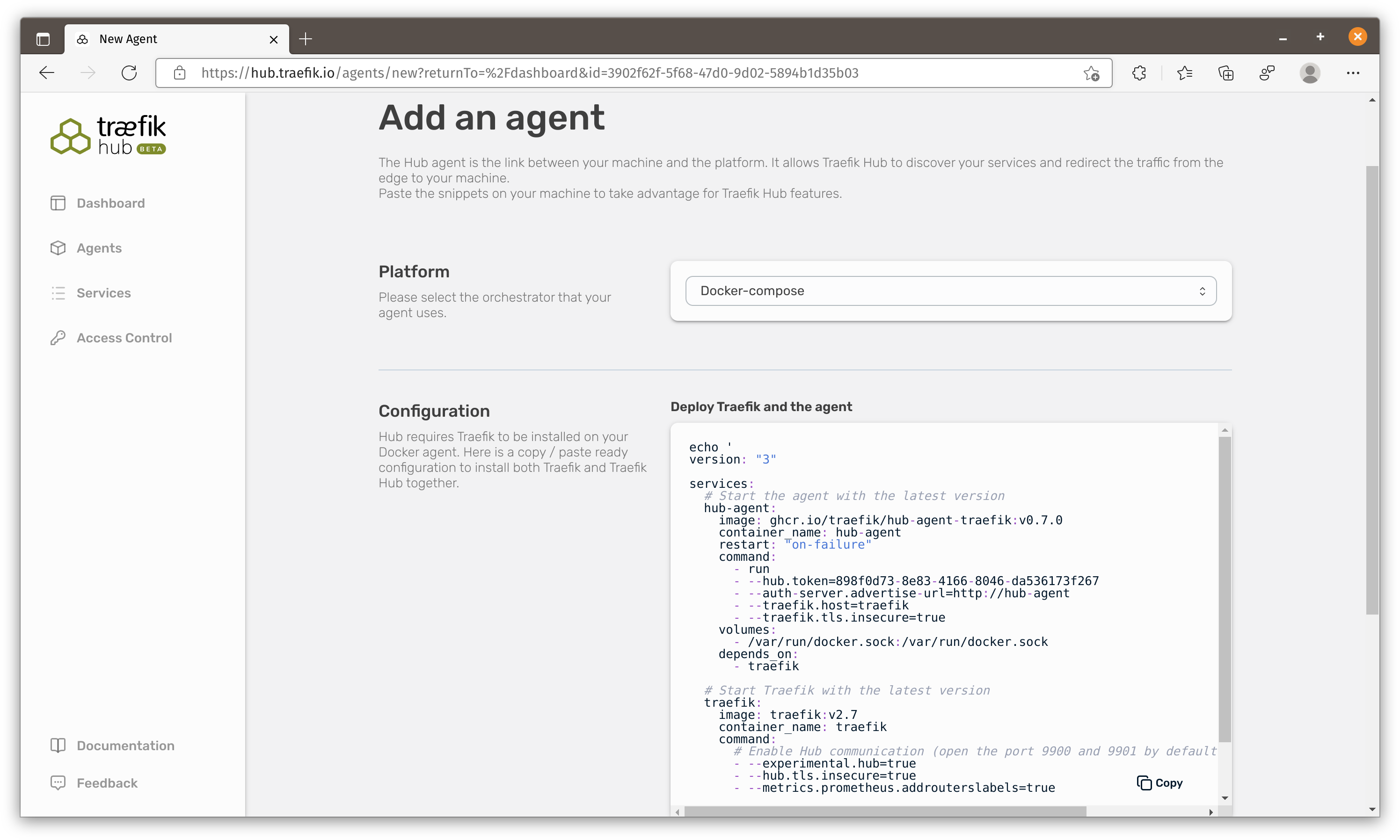
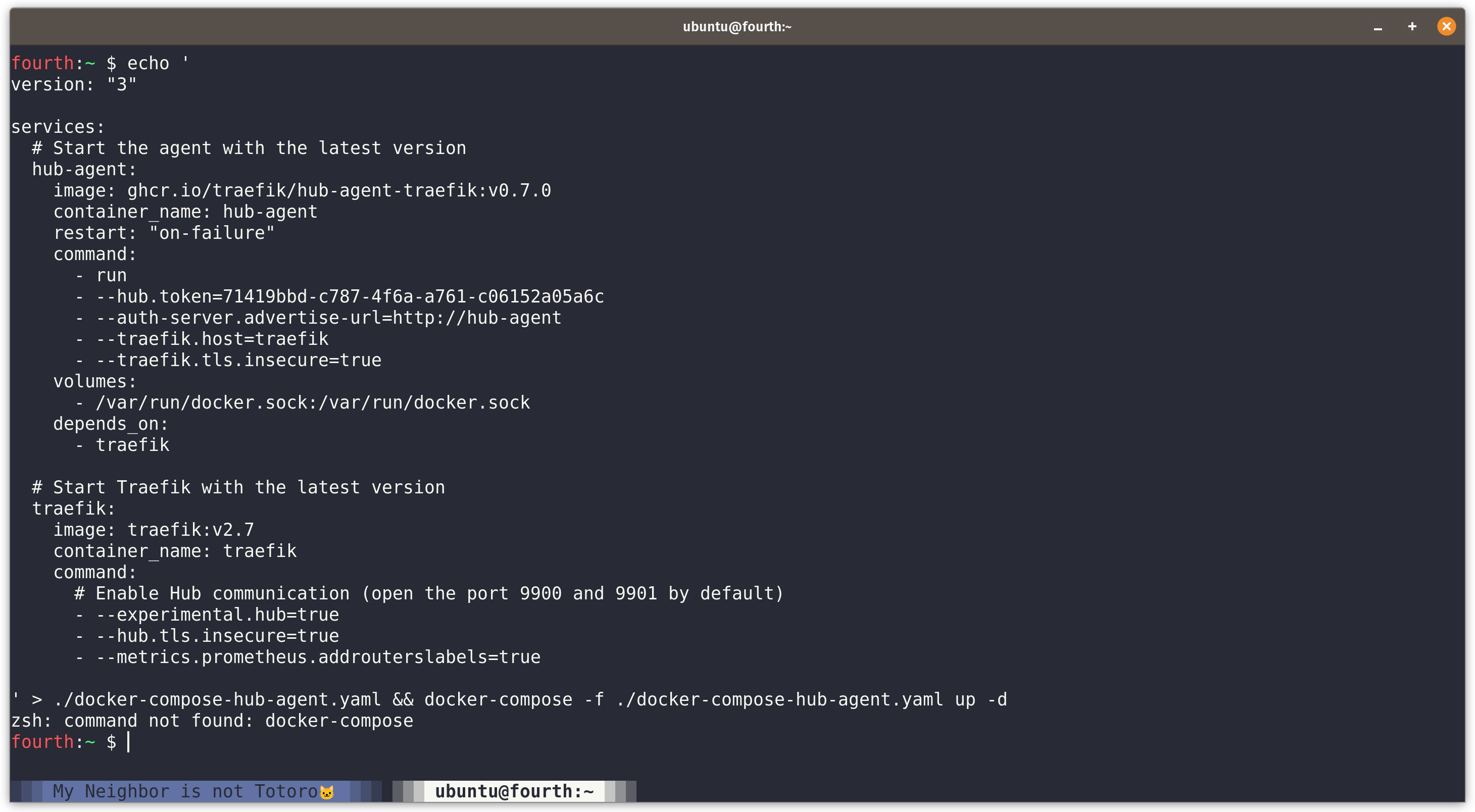
Let’s copy the script and run it on our Virtual Machine. This command saves docker-compose-hub-agent.yaml to current folder and run docker-compose command to start both containers.
First Problem
I quickly ran into my first problem. This command uses docker-compose to start containers but I am using docker compose v2. Compose V2 had been GA from April this year, there will be more and more machines using V2.
It is very important to make sure commands on official doc can be run successfully in as many situations as possible. I suggest Traefik to provide a convenient script to start these containers with docker run command. They can put both script and compose file on their GitHub repo which is easier to track and fix.
Anyway, once the containers are running and Traefik Hub control plane detects the new agent, it would ask you to name this agent.
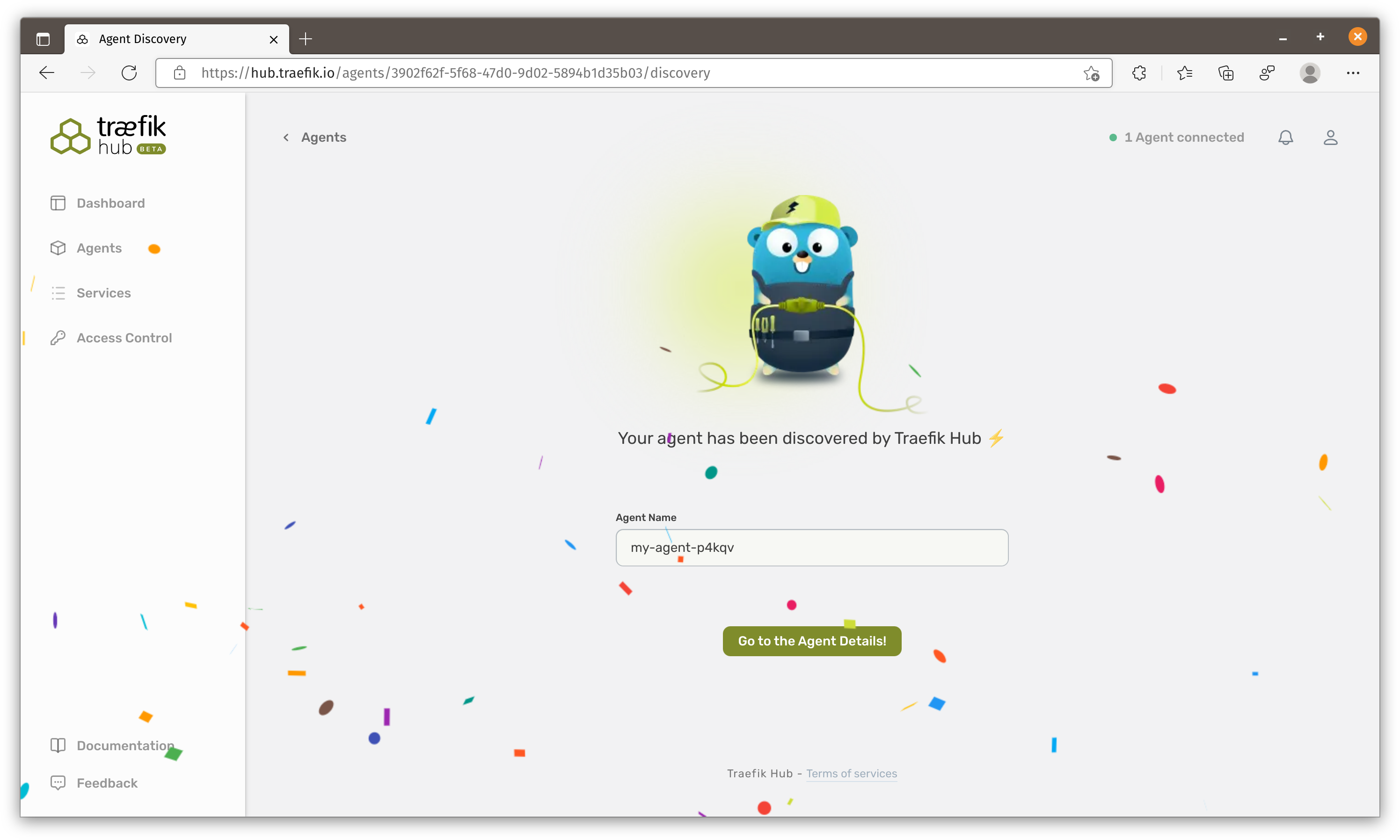
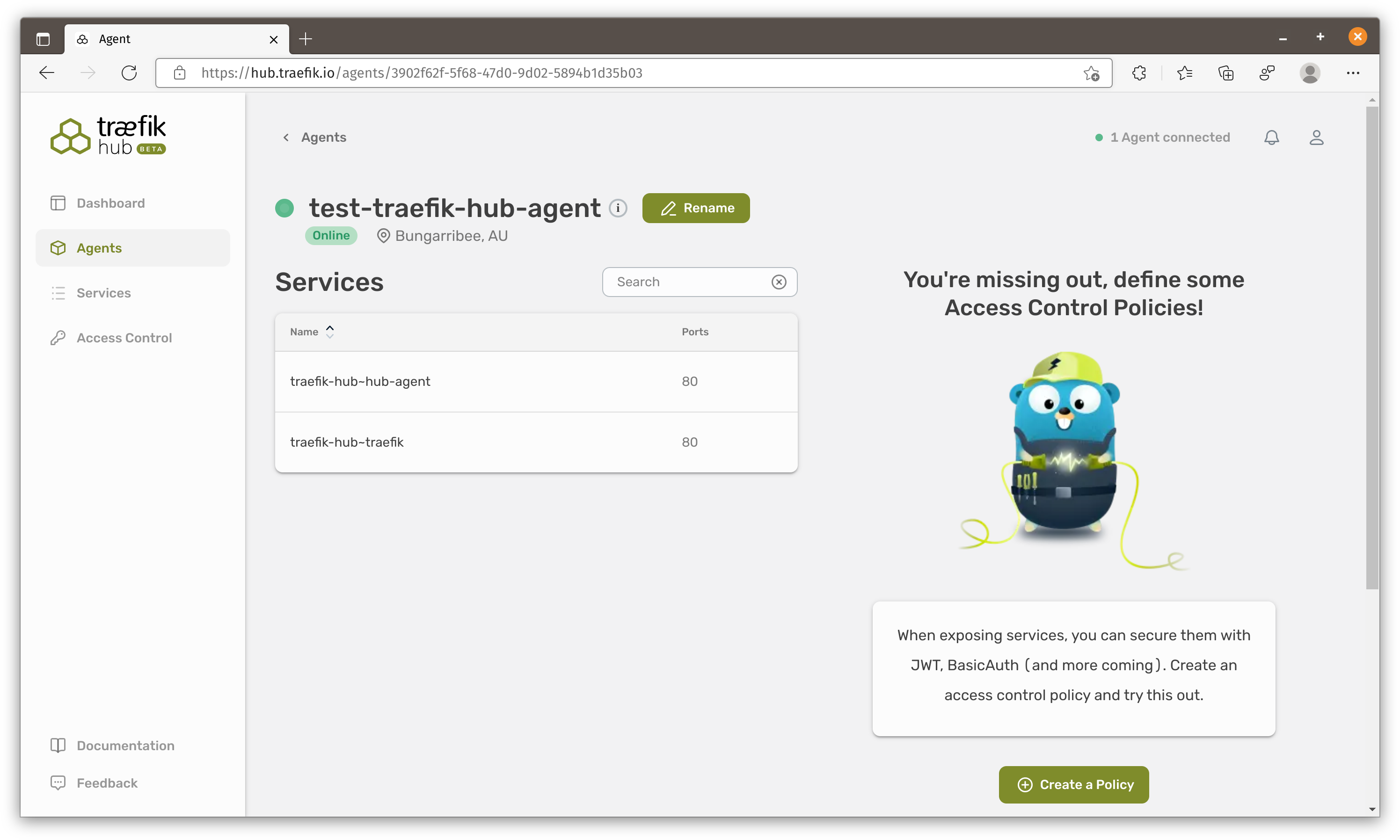
In the agent details and we can see it finds these 2 containers. We can also create policies to be applied on services connected to this agent.
Currently there are only two policies that you can use. One is the BasicAuth and the other one is Traefik Enterprise JWT Auth.
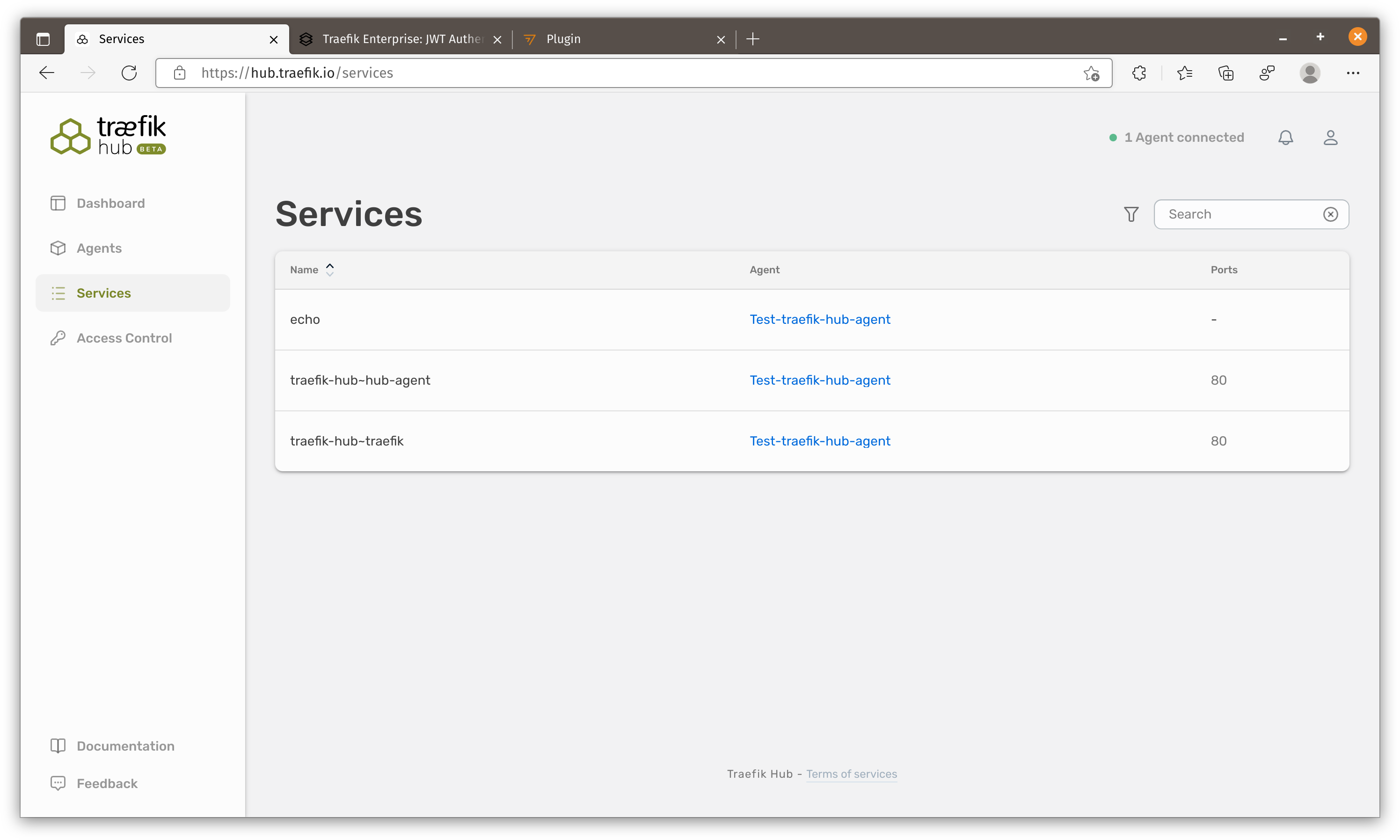
Create first service
Now it is time to create our first container.
1 | docker run --name echo --rm --detach ealen/echo-server |
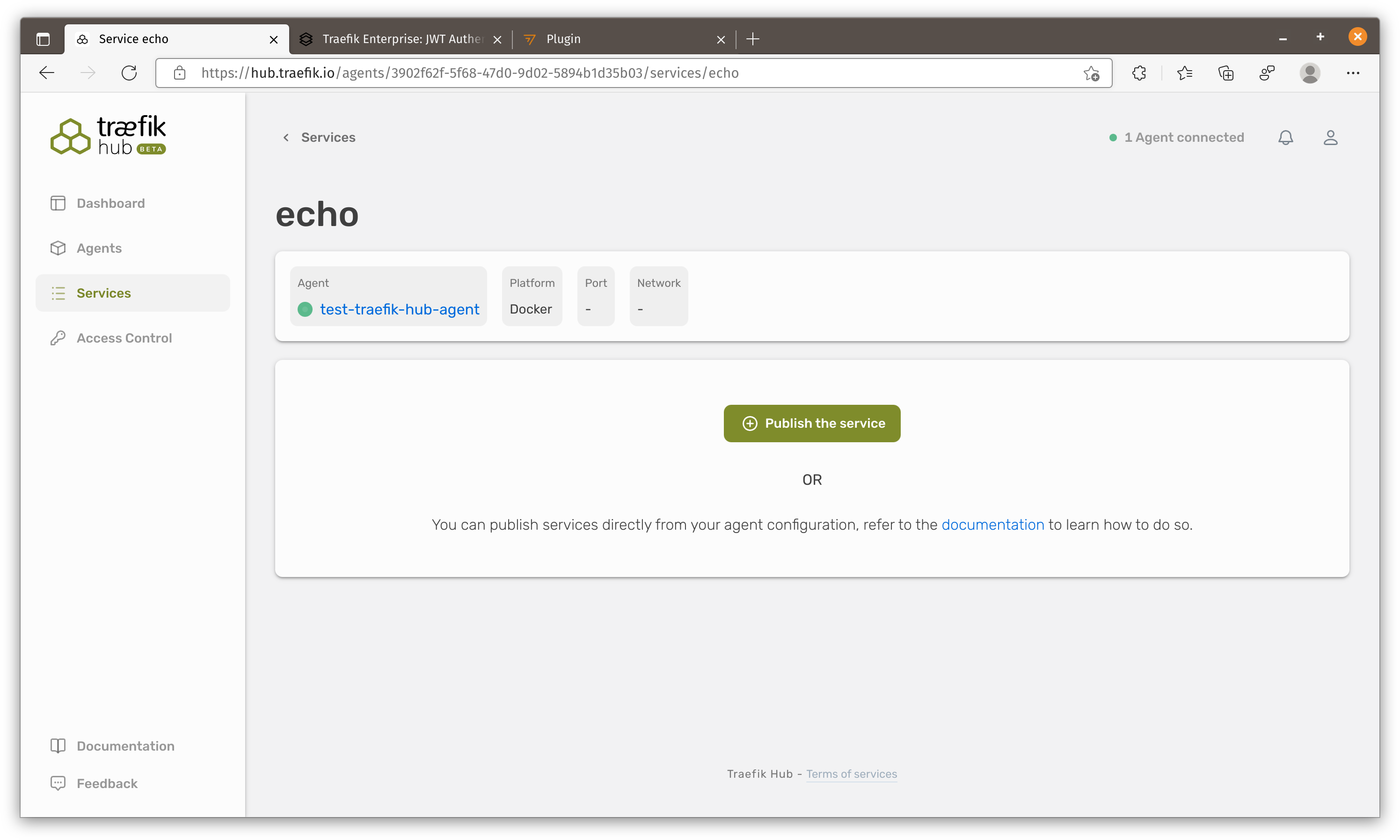
We will see this service showing and let’s publish this service.
Second Problem
Here comes the second problem. Traefik agent discover containers from querying docker engine API which means it can find all docker containers but traefik (the other container) CANNOT access containers in different networks.
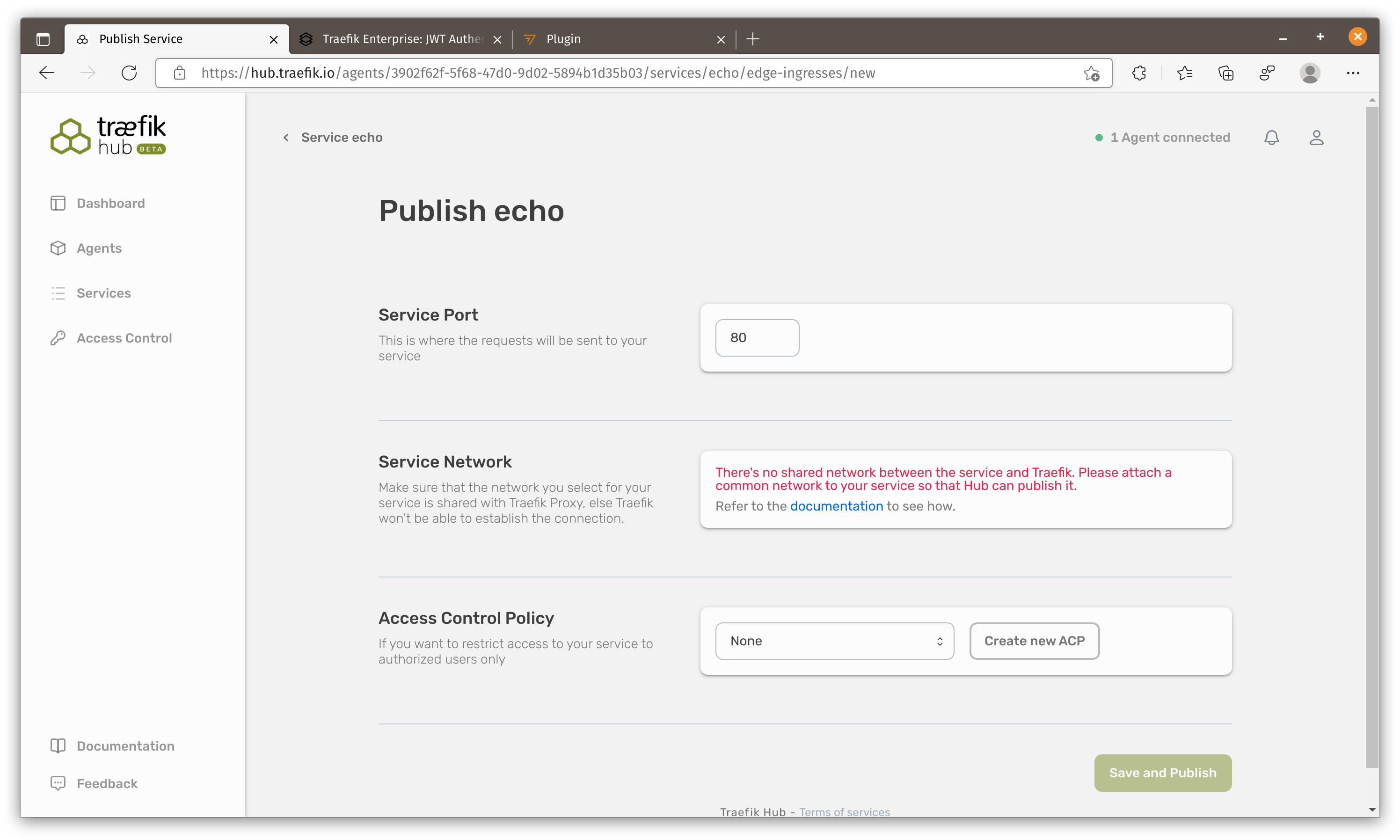
Let’s re-run our container and put it in the same docker network.
1 | docker run --name echo --rm --detach --network ubuntu_default ealen/echo-server |
After publishing our service Traefik hub would generate a URL automatically.
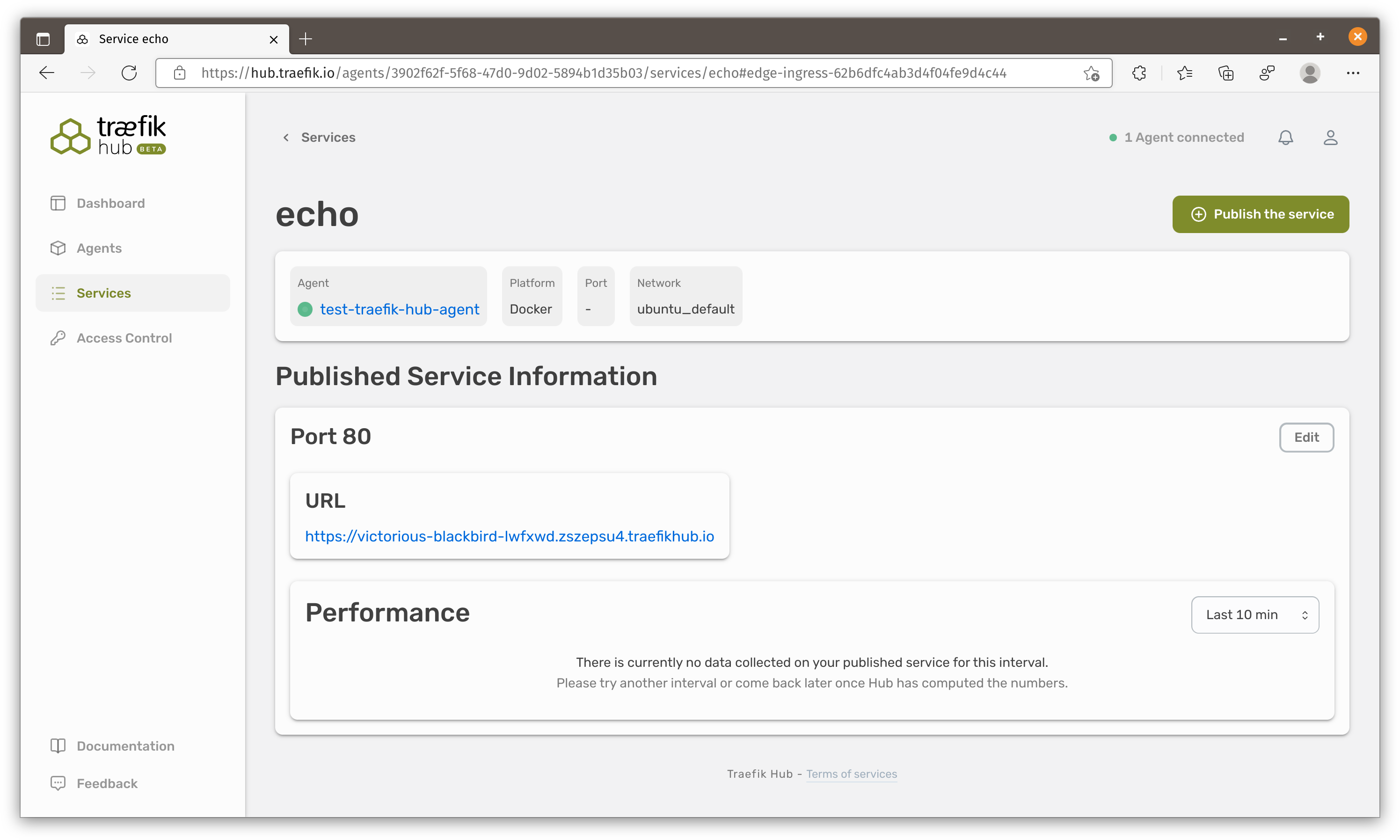
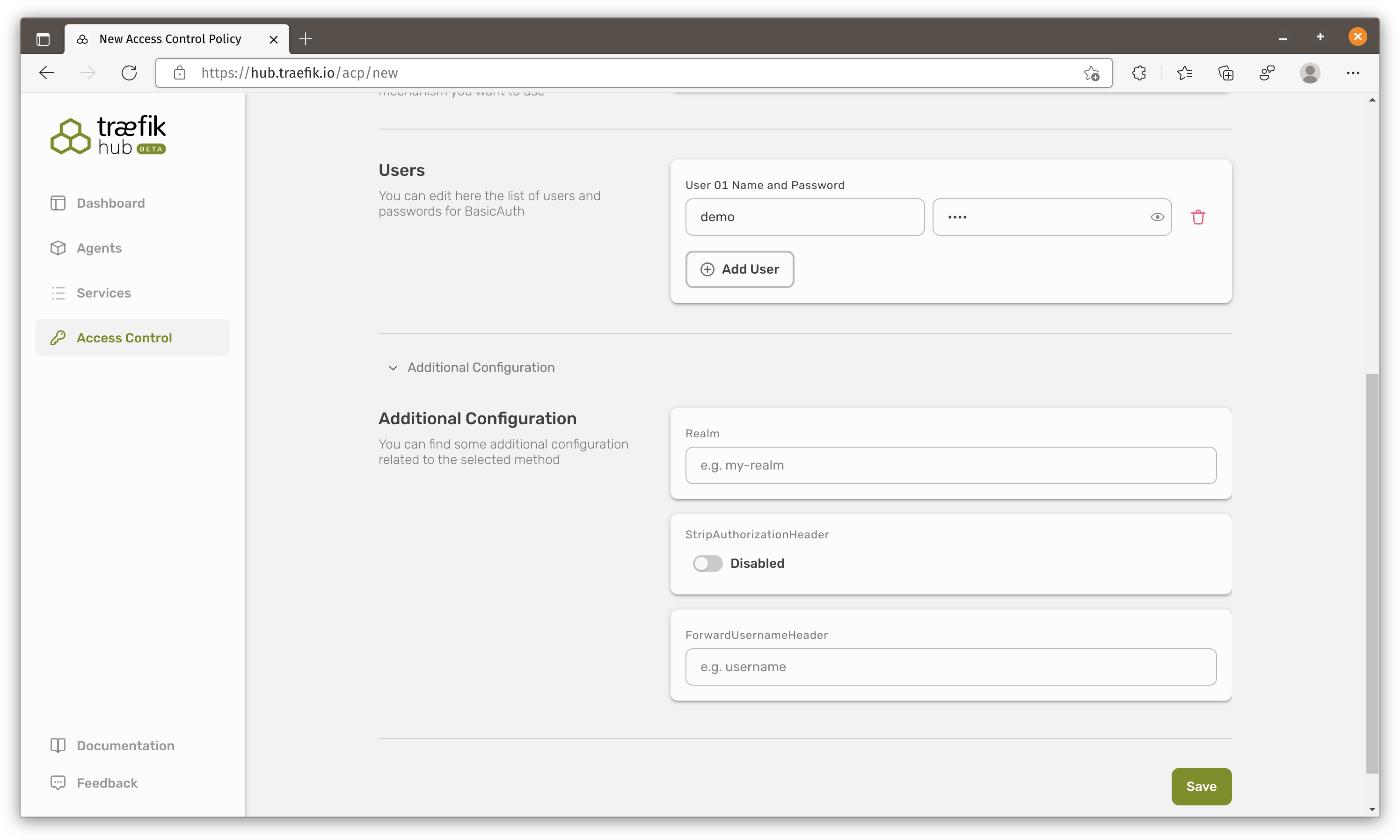
Apply BasicAuth policy
Creating and applying policy to service is very straight forward. I think it just creates a BasicAuth middleware and apply it on the service. I will leave JWT auth for you to explore.
Once we enter the correct username/password, we are allowed to go in.
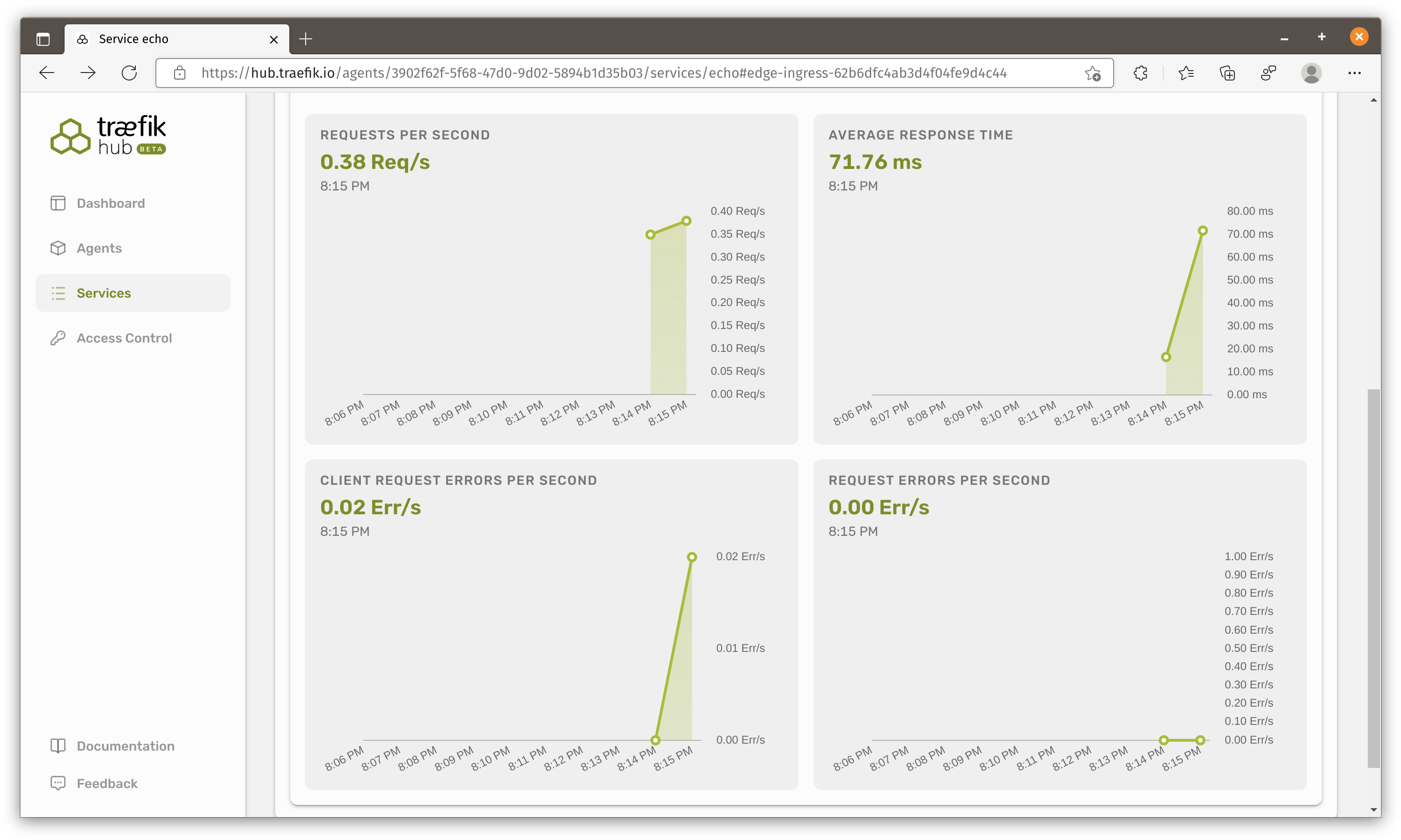
Monitoring
Summary
That’s about all features that I can find and test. To be honest, even it is in Beta, I am still quite disappointed of how little features this product has at this moment. I think they can polish it a little bit more.
For example, what’s the point of having a link to the doc when documentation is not available?
The Quotas section in settings suggests Traefik might want to charge users for the number of services and bandwidth.
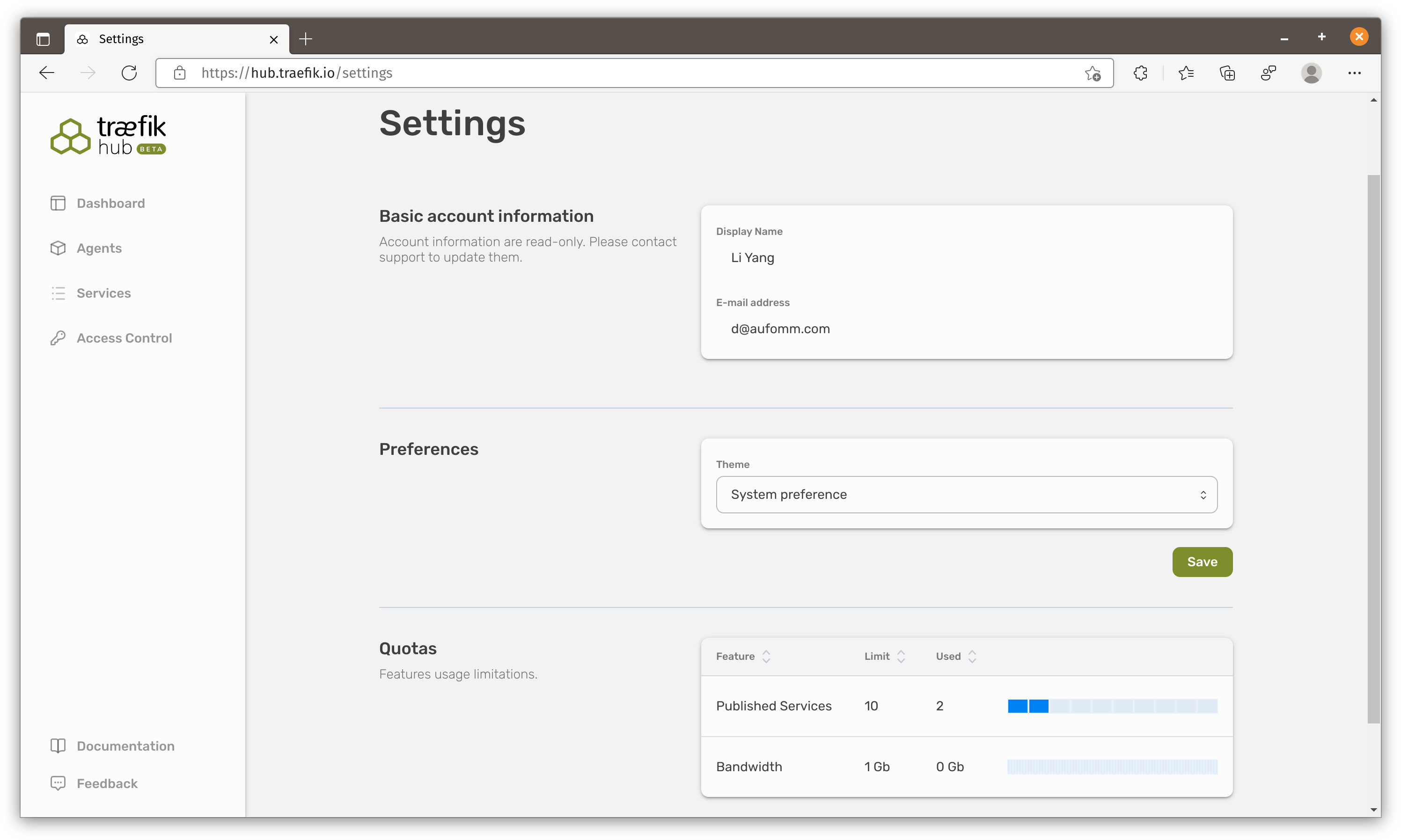
People will only try and stay with a product when it has the same level of basic feature and they will only pay for the UNIQUE features. Frankly I don’t think JWT auth is a good differentiator here especially when basic features are missing.
For example:
- No binaries nor the ability to change service name to IP which means you can’t expose services running on host.
- No custom domain.
- No TCP connection.
- No Geo info of their Edge network entry point nor the ability to change that.
No matter these are free or paid features, they are critical if Traefik wants to enter this marketplace.
I think it is easy enough for Traefik to bring their Enterprise middlewares to the picture which should help building the product differentiation but they really need to work on the basic features. I hope the next time I test it, it would be a more complete and useful product.
That’s all I want to share today, see you next time.